Growing danger: Hacking as a business model – Article in NEW BUSINESS magazine
It pays to think about IT security strategically and holistically.

The threat posed by targeted cyberattacks continues to escalate for companies, as shown by recent studies by the European Union Agency for Cybersecurity (ENISA): According to the Threat Landscape Report 2024, there has been a significant increase in cyber incidents in the EU—11,079 cases in the first half of 2024. Hacking is no longer a marginal phenomenon, but a lucrative business model for organized groups – with professional structures, a division of labor, and increasingly sophisticated attack methods.
Amidst this development, the deadline for implementing the EU's NIS2 directive to increase the cybersecurity of companies and institutions in the European Union – for companies in critical sectors – is approaching. The consequence: many organizations need to take action to strengthen their IT security quickly and sustainably. But even for companies that are not yet subject to the NIS2 regulation, a strategically thought-out and resilient security approach is worthwhile. This is because cyberattacks are increasingly targeting SMEs and smaller businesses – often deliberately, as they often lack effective protection mechanisms.
Sphinx protects against cyber attacks with comprehensive IT security.
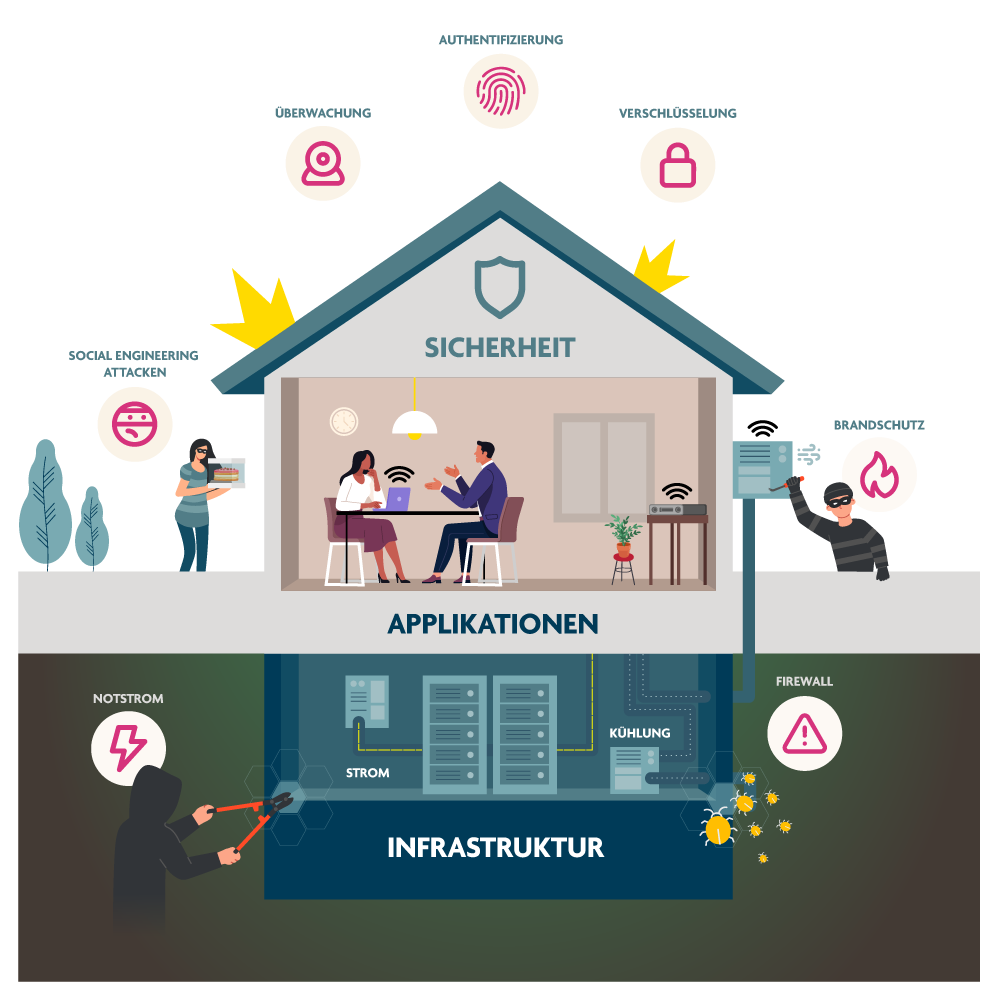
Comprehensive IT security architecture instead of piecemeal patchwork
“Every day, we see how real the risk of cyber attacks has become – from production stoppages in industrial companies to data leaks costing service providers millions,” says Bernd Schellnast, Head of Operations and member of the management board at Sphinx IT Consulting. “Our response to this is a comprehensive and practical security approach that encompasses not only technology, but also processes and people within companies.”
Instead of relying on individual measures, Sphinx relies on an integrated security model. The approach covers all levels of the IT landscape – from infrastructure to user interface. The five core areas of the Sphinx security architecture – infrastructure protection, secure applications, data security, active monitoring, and awareness training – are interlinked, providing a comprehensive protective shield for companies of all sizes. “The question is not whether an attack will come, but when – and how well you are prepared. Those who only take selective action run the risk of overlooking dangerous gaps,” says Schellnast.