Sometimes good is here 19.20 Windows Patch
One of the challenges faced by database administrators and developers is ensuring secure communication between the database client and the server. Oracle’s Advanced Networking Option (ANO) provides robust security features, including the ability to encrypt connections. Here’s a guide based on a tested configuration to set up SSL using Oracle’s tools.
Prerequisites:
- Ensure you have Oracle Client Version 19.14 or higher, as this configuration doesn’t require a wallet on the client side.
- This setup is referenced from Oracle’s documentation Doc. 2889040.1.
Setup Steps:
1. On the Server Side:
a. Create the CA/ROOT certificate:
orapki wallet create -wallet /app_oracle/admin/network/sslroot -pwd longpwd
orapki wallet add -wallet /app_oracle/admin/network/sslroot -dn C=US,CN=ROOT -keysize 1024 -self_signed -validity 3650 -pwd longpwd
orapki wallet export -wallet /app_oracle/admin/network/sslroot -dn C=US,CN=ROOT -cert /app_oracle/admin/network/sslroot/cacertificate.txt -pwd longpwdb. Create the SERVER certificate:
orapki wallet create -wallet /app_oracle/admin/network/sslserver -auto_login -pwd longpwd
orapki wallet add -wallet /app_oracle/admin/network/sslserver -dn C=US,O=org,CN=serverhostname.com -keysize 1024 -pwd longpwd
orapki wallet export -wallet /app_oracle/admin/network/sslserver -dn C=US,O=org,CN=serverhostname.com -request /app_oracle/admin/network/sslserver/creq.txt -pwd longpwd
orapki cert create -wallet /app_oracle/admin/network/sslroot -request /app_oracle/admin/network/sslserver/creq.txt -cert /app_oracle/admin/network/sslserver/cert.txt -validity 3650 -pwd longpwd
orapki wallet add -wallet /app_oracle/admin/network/sslserver -trusted_cert -cert /app_oracle/admin/network/sslroot/cacertificate.txt -pwd longpwd
orapki wallet add -wallet /app_oracle/admin/network/sslserver -user_cert -cert /app_oracle/admin/network/sslserver/cert.txt -pwd longpwdc. Configuration on the Server:
In listener.ora:
# added 2484 as tcps
SSL_CLIENT_AUTHENTICATION = FALSE
WALLET_LOCATION=
(SOURCE=
(METHOD=FILE)
(METHOD_DATA=
(DIRECTORY=/app_oracle/admin/network/sslserver/)))
C10P1 =
(DESCRIPTION_LIST =
(DESCRIPTION =
(ADDRESS = (PROTOCOL = TCP)(HOST = serverhostname.com)(PORT = 1521))
(ADDRESS = (PROTOCOL = TCPS)(HOST = serverhostname.com)(PORT = 2484))
)
)In sqlnet.ora:
# FOR TLS Encryption
SQLNET.AUTHENTICATION_SERVICES = (TCPS,NTS,BEQ)
SSL_CLIENT_AUTHENTICATION = FALSE
WALLET_LOCATION = (SOURCE =
(METHOD = FILE)
(METHOD_DATA = (DIRECTORY = /app_oracle/admin/network/sslserver/)))
# for Oracle NATIVE ENCRYPTION:
SQLNET.ENCRYPTION_SERVER = REQUIRED
SQLNET.ENCRYPTION_TYPES_SERVER = (AES256)
SQLNET.CRYPTO_CHECKSUM_SERVER = REQUIRED
SQLNET.CRYPTO_CHECKSUM_TYPES_SERVER = (SHA384)
IGNORE_ANO_ENCRYPTION_FOR_TCPS=TRUE2. On the Windows Client:
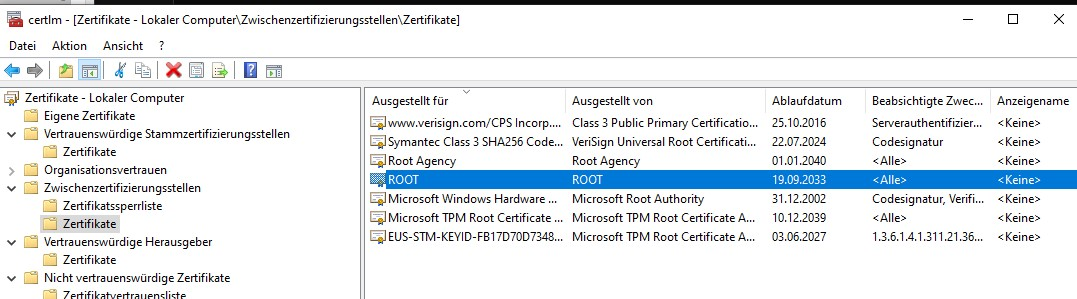
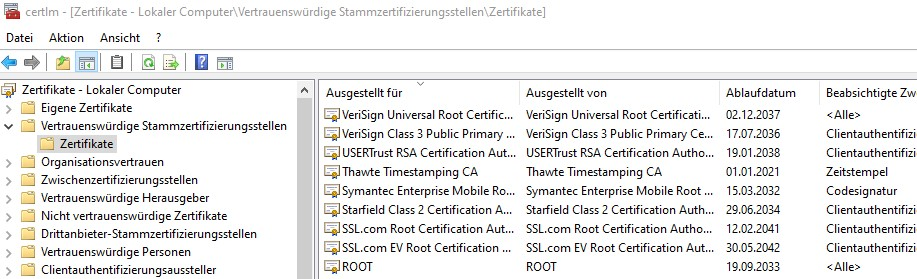
a. Rename cacertificate.txt to cacertificate.crt. Right-click on the CRT file and choose ‚Install Certificate‘ in Windows Explorer. After that you have t move via certlm the cert into trusted root folder
b. For clients update sqlnet.ora:
SSL_CLIENT_AUTHENTICATION = FALSEAnd tnsnames.ora:
TLS / SSL connection without using a client side Wallet (Doc ID 2889040.1)
swingbenchtls = (description=(address=(protocol=tcps)(host=serverhostname.com)(port=2484))(connect_data=(service_name=SWINGBENCH))(SECURITY=(MY_WALLET_DIRECTORY=SYSTEM)))
(SECURITY= .. is not really needed.. but a good information indeed )Test the connection using:
sqlplus system/goodoldsystempwd@swingbenchtlsIf facing issues with certificate location, check the certificate manager (certlm) and move the certificate to the ‚Trusted Root Certification Authorities‘ folder.
3. On the Linux Client:
a. Use the same sqlnet.ora and tnsnames.ora configurations as in the Windows client.
b. Add cacertificate.txt to /etc/pki/tls/cert.pem.
Now, testing should confirm a successful TCPS connection. When querying for the protocol, the expected result is:
select sys_context ('userenv','network_protocol') from dual;Output: tcps
In conclusion, using Oracle’s tools and utilities, we can effectively secure the connection between our database client and server. Always ensure you’re following best practices and referencing official Oracle documentation where needed.

